
The amazing growth of cryptocurrency has all along been hampered by hacks, scams & fraudulent activities since its introduction. According to Cryptoaware, more than US$2 billion has been reported as loss to scams and hacks. Kaspersky Labs, a cybersecurity firm, reported that cryptocurrency scammers stole around $2.3 million dollars, in Q2 2018. Don't be a victim of crypto scams. Here is the comprehensive list of scams, and how to avoid them.
1. Fraudulent ICOs and Fake Giveaways
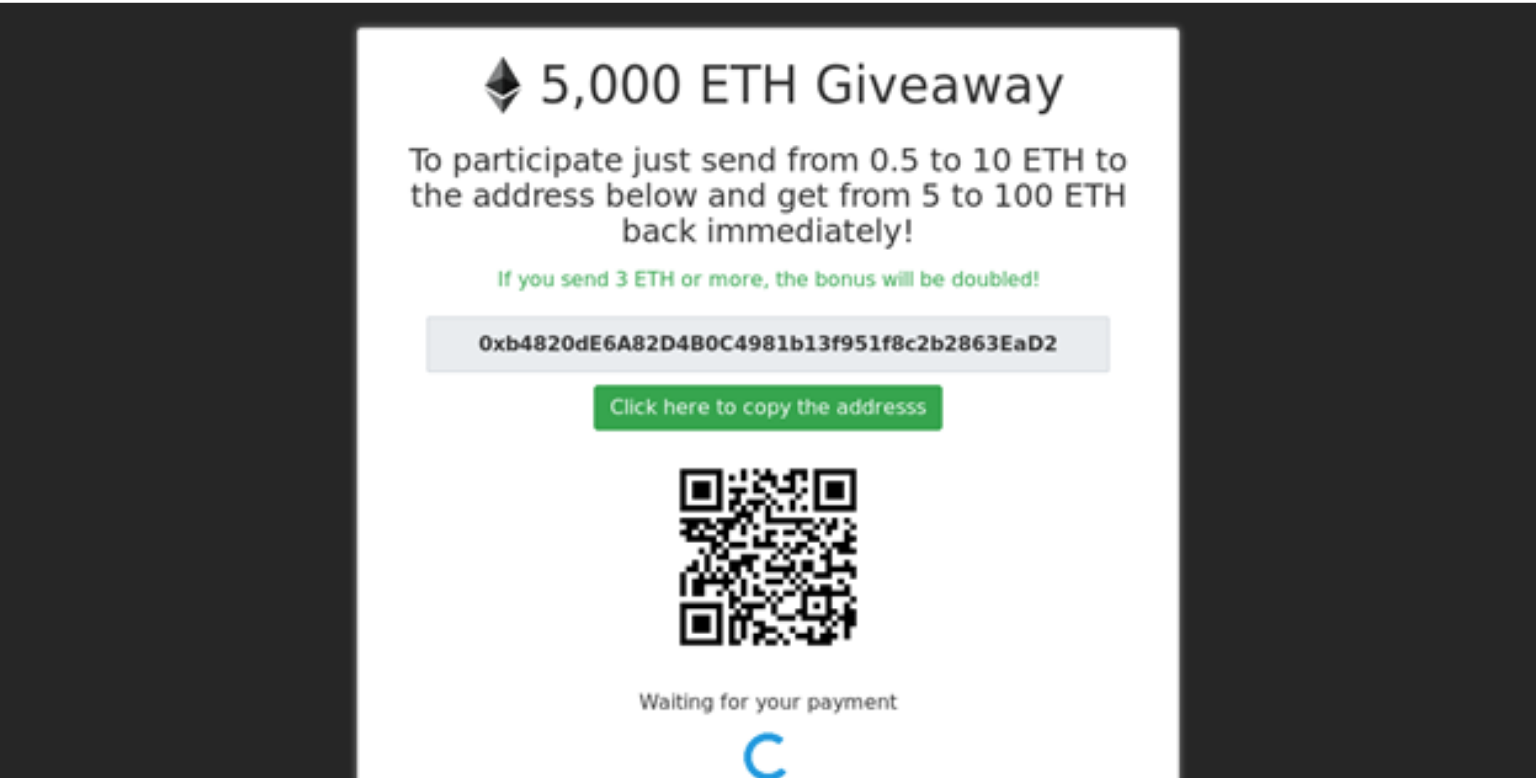
The easiest way to pull of a scam is to build and market a fraudulent Initial Coin Offering project. ICOs have been an important way for legitimate businesses to find the necessary funding through crowd-funding. Many fraudulent ICOs simply write a whitepaper, develop a marketing campaign on social media, list the token on exchanges and conduct a fake airdrop or token sale. As such, many new investors are scammed into the promise of earning 1000% gains from these ICOs, but end up buying worthless tokens.
How to avoid fraudulent ICOs / Token Sales:
- Check the quality of Whitepaper - Are the promised returns too good to be true? Is it filled with errors?
- Is there a legitimate road map for the token and a proof of concept?
- Ask hard questions about the project - Does the team ignore it or answer your questions?
- Check the exchange that the coin is listed on - Does it have a sizeable trade volume?
- Share and discuss it with friends or a community - Ask them if they think it’s a scam.
2. Unregulated brokers and exchanges
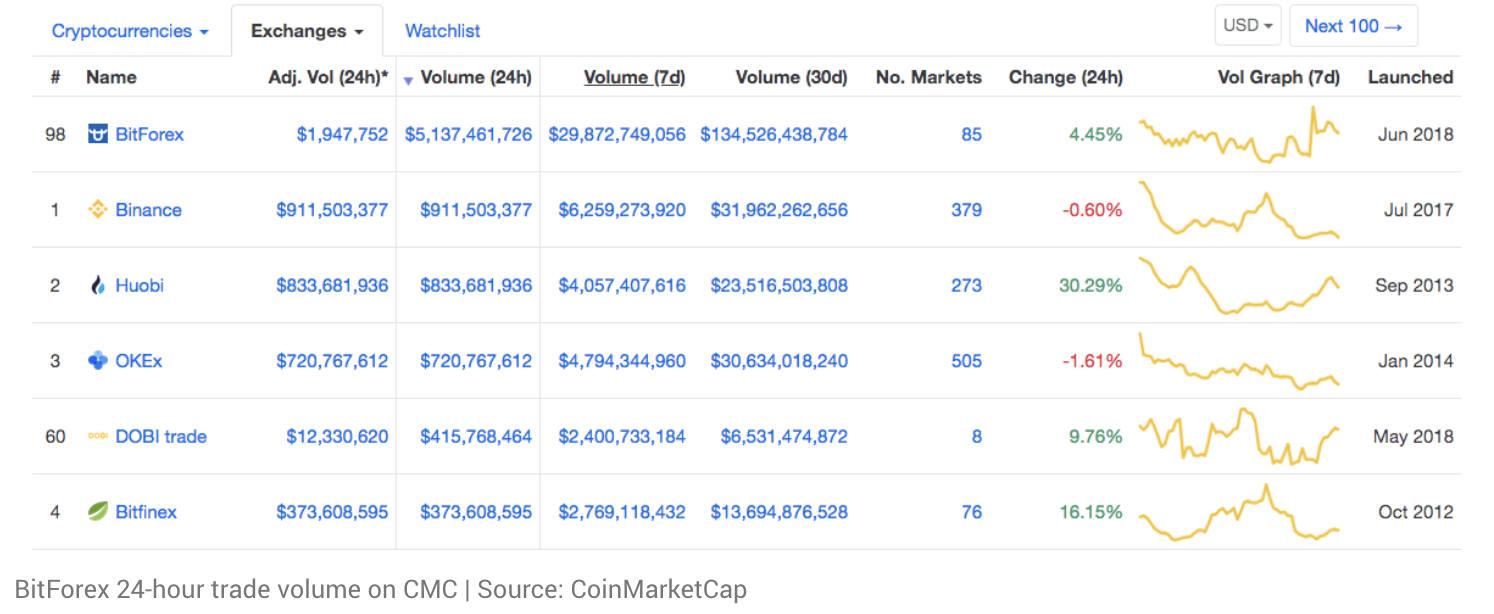
The cryptocurrency world is filled with shady exchanges that appear and disappear overnight. One needs to be very careful about these exchanges because they may simply disappear with your tokens or your money. Alternatively, once you deposit money, some of these exchanges will charge you outrageous commissions or make it very difficult for you to withdraw your funds.
Additionally, some of these exchanges make it really attractive for new traders to use their platform by charging absolutely nothing for transaction fees and trading fees. Instead, they earn their revenue by charging a fee for listing any token (including fraudulent ICOs) on their platform, without ensuring proper trading liquidity for traders to freely buy or sell the tokens. Some of these tokens would eventually get frozen on these exchanges, and traders are stuck with their ‘shit coins’ without a way to liquidate it. Some of these ICO tokens may also introduce security loopholes into the exchange which could jeopardize the security of the entire database.
How to avoid fraudulent exchanges:
- Check if there is a legitimate company address and also for any regulatory authentication
- Check for unrealistic surges in trade volume, especially if the exchange just started operation
- Check if there are any online articles about the exchange
- Is the team working on the exchange being anonymous or transparent about their identities?
- Research on the tokens listed on the exchange to ensure that it is a safe investment
3. Fake wallets
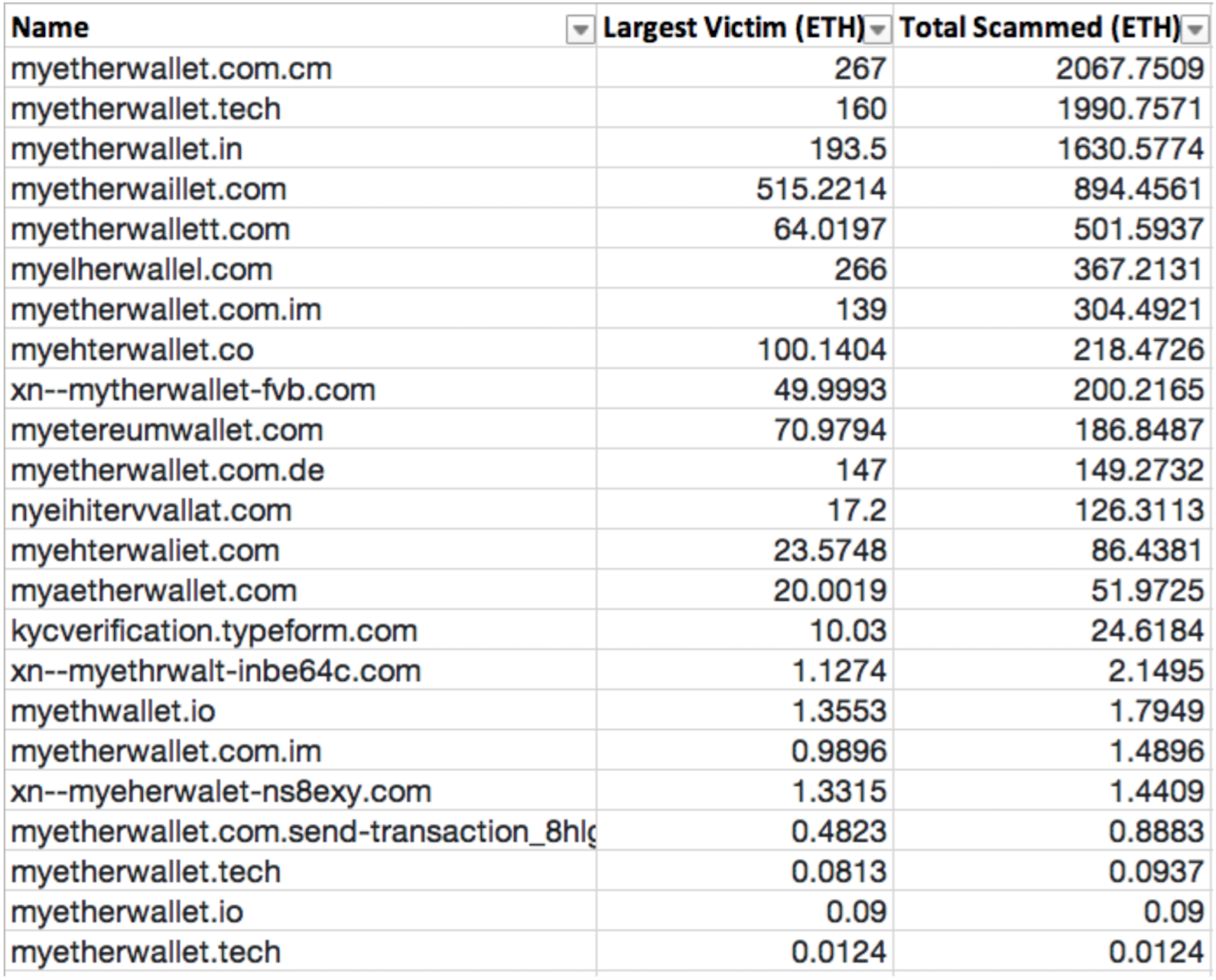
Digital wallets store your cryptocurrency data, private and public keys. Ever since the launch of Bitcoin, many fake iOS, Android and even online software wallets have been launched. Many of these wallets will take your private keys which gives the scammers full access to all your digital assets.
How to avoid fake wallets:
- Check if the digital wallet is supported by key figures in the cryptocurrency industry
- Is the development team being anonymous or transparent about their identities?
- Use hardware wallets (e.g. CoolWallet, Ledger) to store cryptocurrency for longer term
4. Phishing (Fake websites)
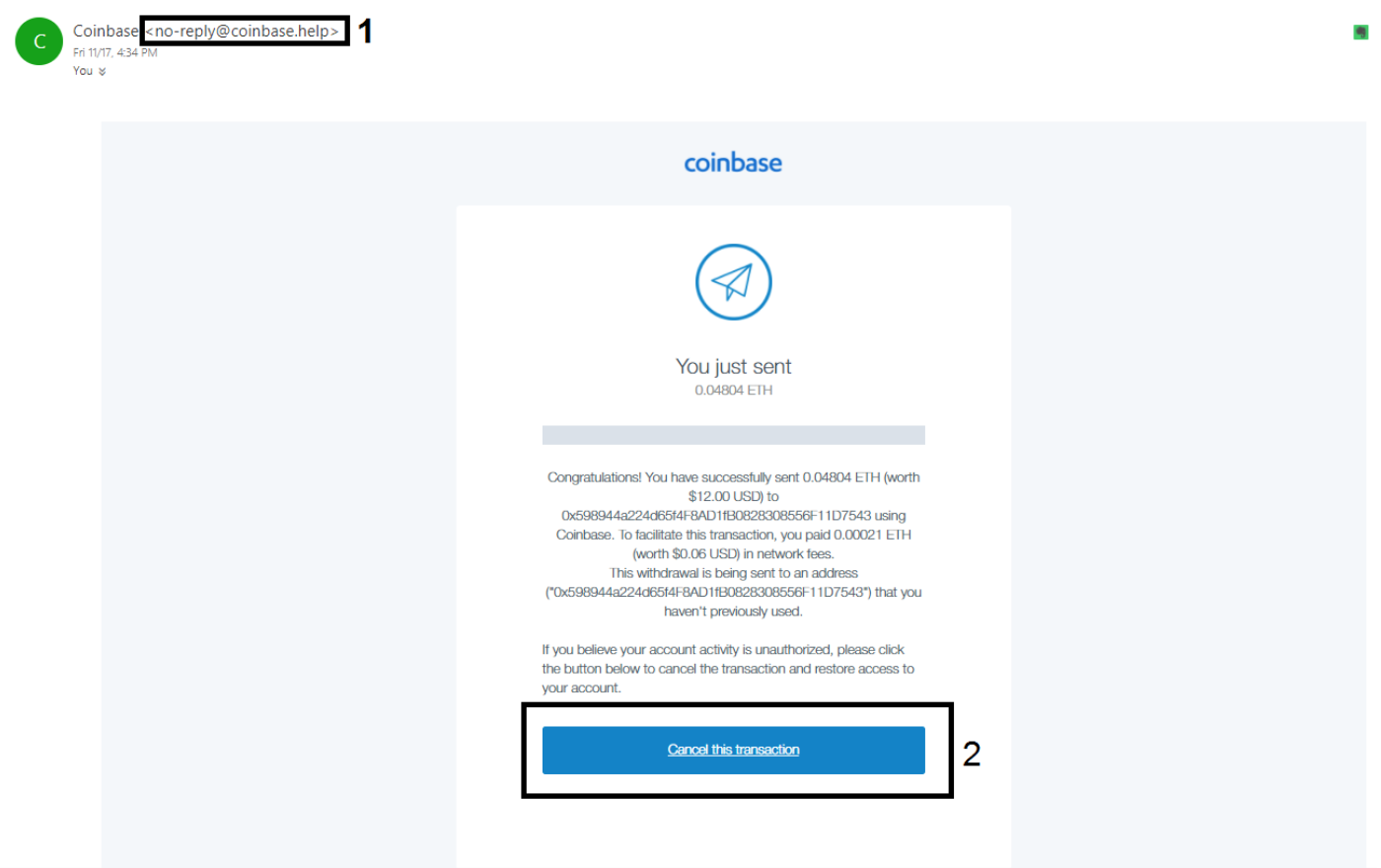
Phishing scams are another very common form of scam in the cryptocurrency sphere. Scammers try to gain access to your username, password, or private keys by fooling you. Their main strategy is to imitate popular cryptocurrency websites and exchanges by purchasing similar web domains (using Punycode). The fake website would look almost identical to the original, but with one main difference: once you key in your details, the platform will record your information and use it to gain access to your real accounts.
How to avoid phishing:
- Always check the URL that is typed in or type it in personally
- Activate multi-factor authentication (e.g. Google authenticator)
5. Fake identities & Impersonators
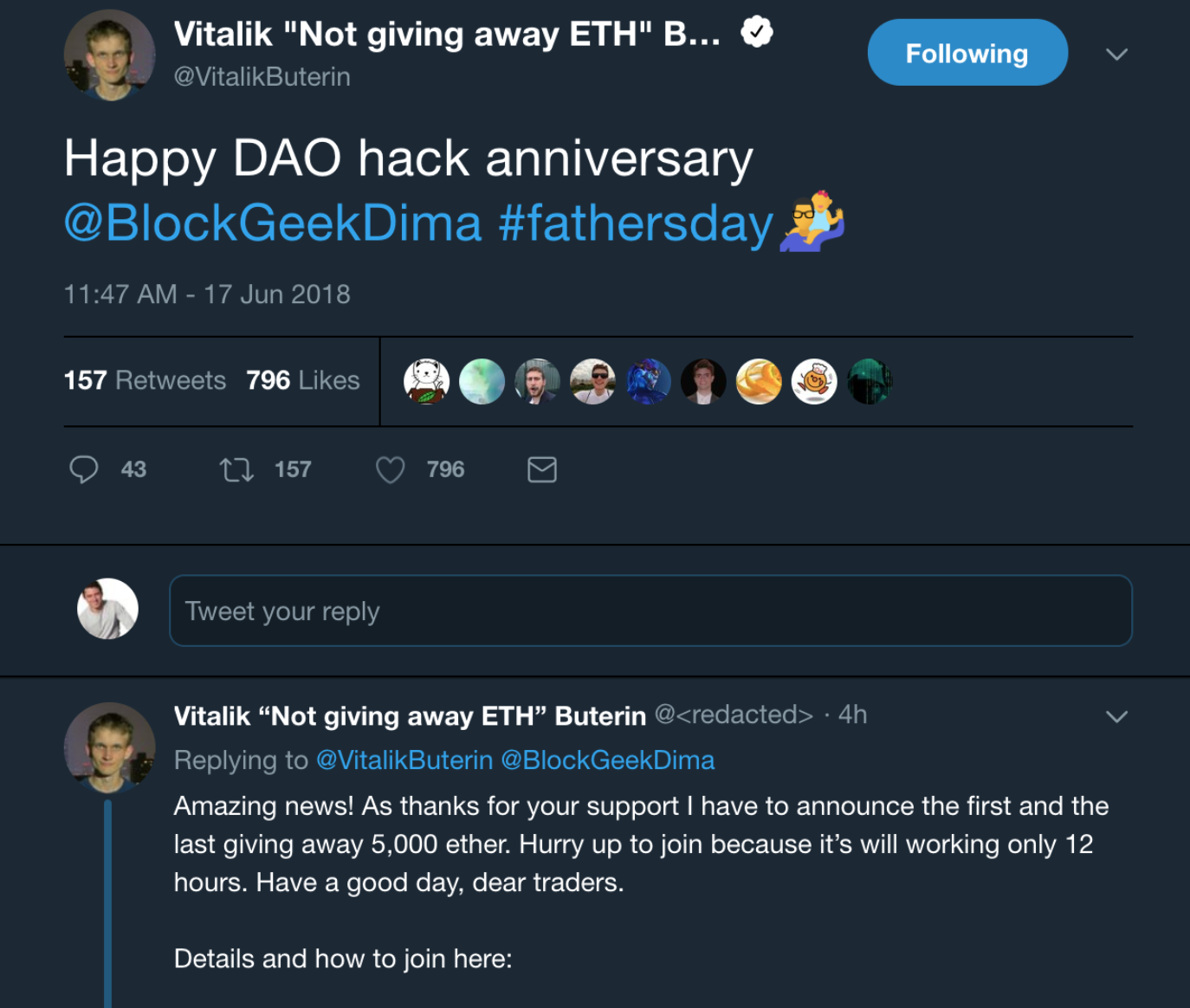
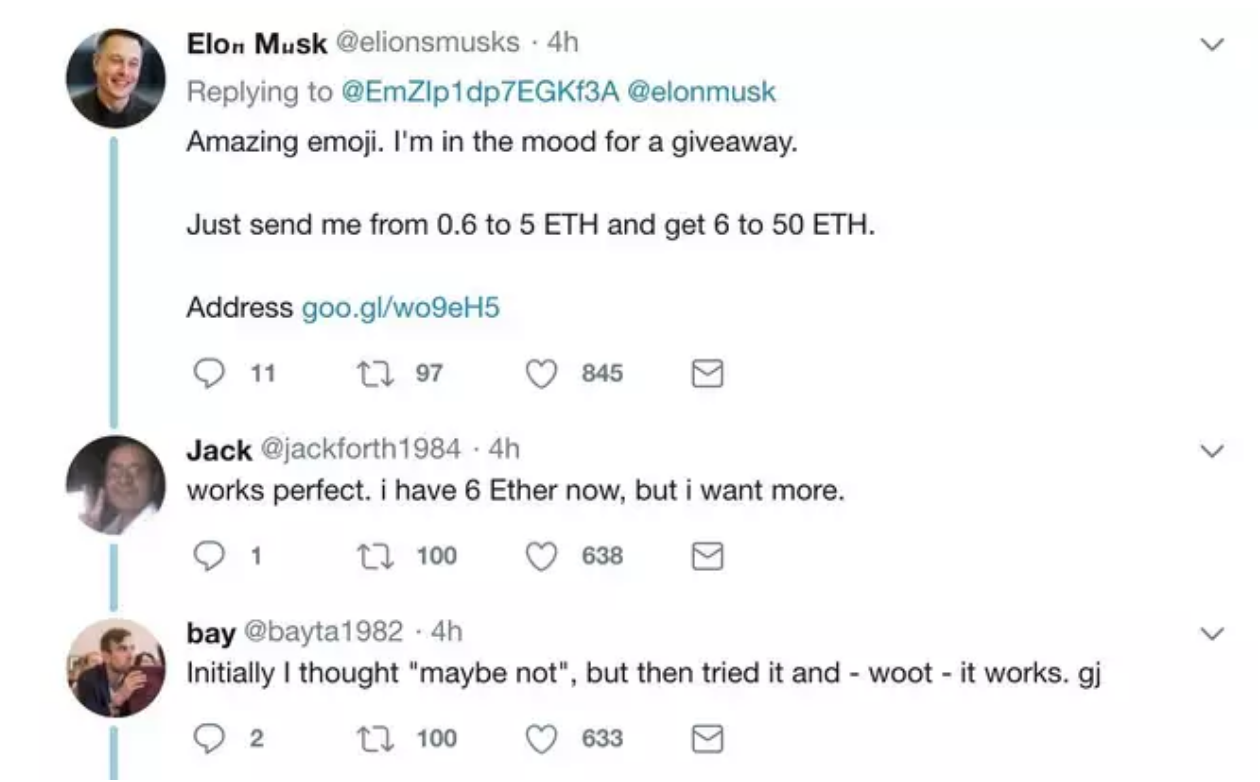
Scammers usually use fake social media accounts to impersonate key figures in the cryptocurrency world. They will create a fake account, with similar social media handles and profile pictures to trick users into investing in illegitimate projects or trick them into giving them their private keys for a reward.
How to avoid these impersonators:
- Check the social media handle thoroughly
- Verify the information with the official cryptocurrency exchange
- Never ever give anyone your private key
6. Pump and Dump groups
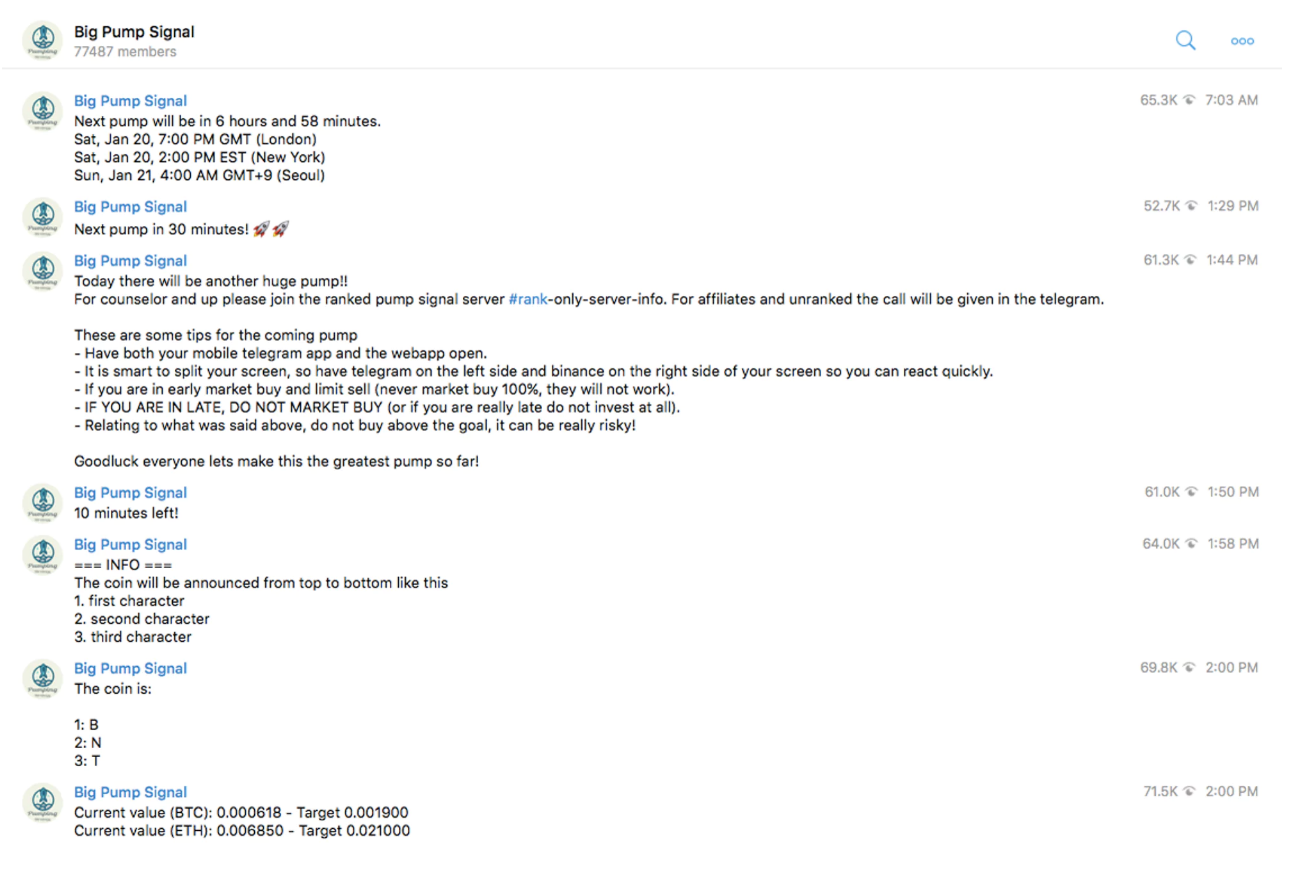
These groups manipulate the prices of altcoins that have low market caps by creating ‘fake hype’ for a digital token by unrealistically driving up its value and trade volumes, before they dump it completely and take a nice profit from it. Traders who act first would take the profits and the people who are a bit late suffer the plummeting prices in just a matter of minutes. They often operate in Telegram or Slack groups. Although this seems like an opportunity to make quick money, most the time, normal traders are slower than these groups that manipulate the market illegally.
How to avoid pump and dump groups:
- Do not participate in these groups (even if they approach you on social media)
- Be wary of tokens that have a sudden and immediate surge in trade volume
7. Pyramid or Ponzi Schemes
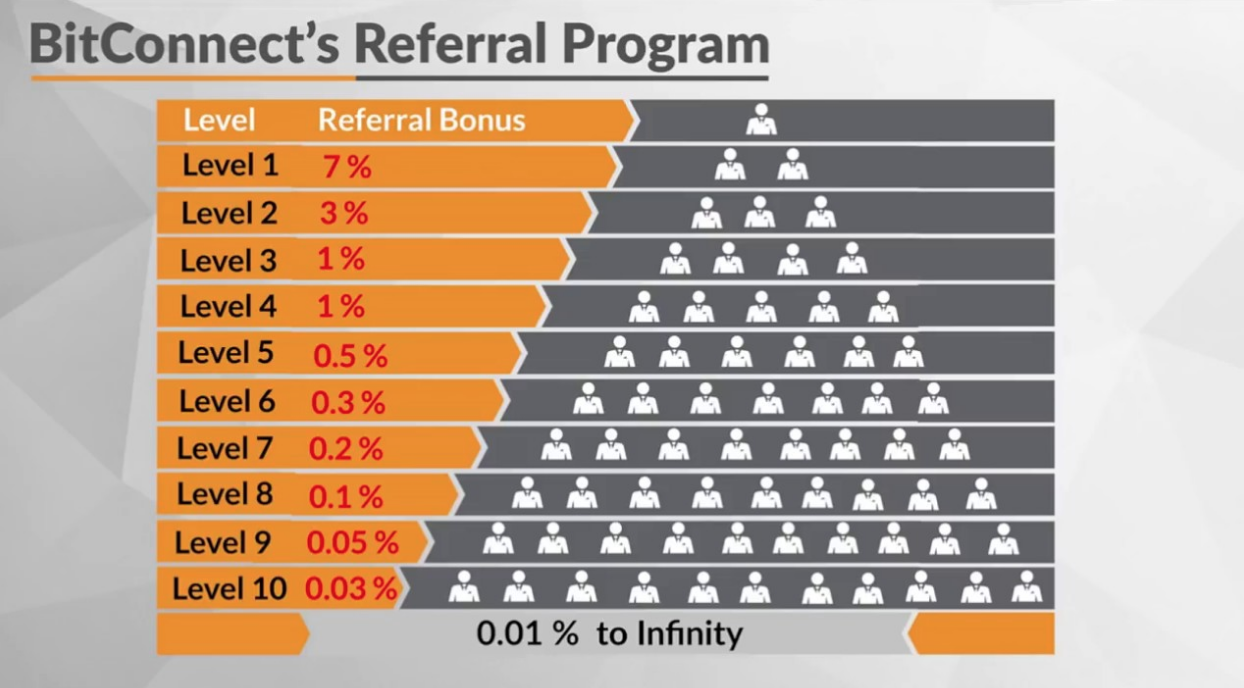
These cryptocurrency projects and platforms often promises returns of investments that are better than the actual cryptocurrency market growth. It usually focuses on recruiting new users to sign up to maximize your own profits. This system usually works on a multi-level marketing model that disguises itself as an investment scheme but it actually just scams the person who enters the system later. Some examples of illegal Ponzi schemes are: BitConnect, Centratech
How to avoid these Ponzi schemes:
- Check if these schemes focus on recruiting new users to grow your own profits
- See if they promise better investment yield than the actual cryptocurrency market growth
8. Malware downloads
The internet has allowed anonymous scammers and hackers to introduce viruses and malware that could give them access to your private accounts in your hardware devices when you open these programs. Scammers usually send these programs, website links and email attachments, which allow them to access your private information when you open these dangerous files. They would often click bait these links by hiding them as free cryptocurrency giveaways, send it as an important document by official websites, or as malware found in cryptocurrency mining programs.
How to avoid malware downloads:
- Set up your personal firewall and antivirus programs
- Do not open unknown email links, attachments, or download suspicious programs
- Verify the authenticity of the source and the email address that sent you the content
Bottom-line:
- Always check the information thoroughly
- If it is too good to be true, it usually is
- Be careful of social media
- Never give away your passwords or private key

